EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USLAB Fortigate VDOM Configuration
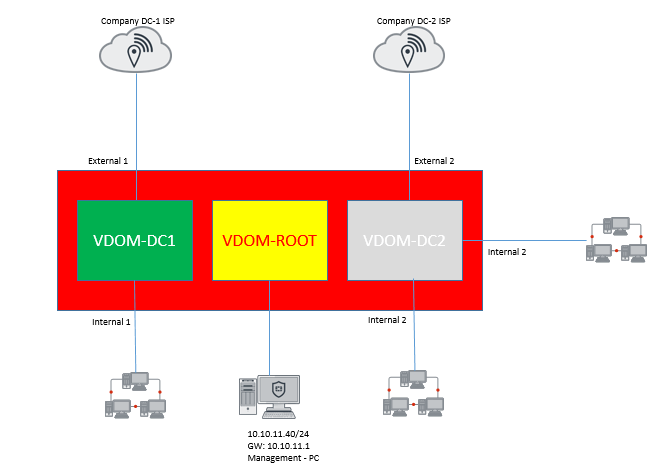
Two companies DC-1 and DC-2 using the same FortiGate with different Internet service providers (ISPs). To provide both corporate and Internet connectivity, each company has its own VDOM (called VDOM DC-1 and VDOM DC-2 ) that are managed independently. The root VDOM will be used to manage the FortiGate's global settings. Let see how Fortigate VDOM is configured by using above scenerios.
Topology :
Task :
Configure the Fortigate as per topology given below.
Solution :
Step1: Switching to Fortigate VDOM mode and creating two VDOMs
Go to the Dashboard and locate the System Information widget. Find Virtual Domain and select Enable. You will be required to re-login after enabling virtual domains
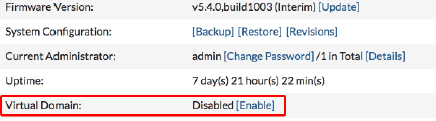
Certain FortiGate models will not show the above option in the System Information widget.Enter the following command in the CLI Console:
config system settings
config system global
set vdom-admin enable
end
Enter y when you are asked if you want to continue.Make sure that Global is selected from dropdown menu located in the top-left corner. This allows you to make changes to the global configuration.
Step2: Create the VDOMS for both customer.
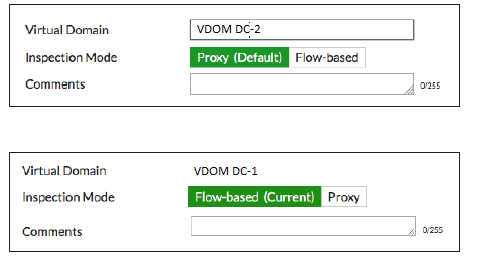
Go to System > VDOM and create two VDOMs: VDOM DC-1 and VDOM DC-2. In this example, the Inspection Mode is set to Proxy for VDOM-DDC2. This will allow this VDOM to use both proxy and flow based security scanning. The Inspection Mode for VDOM DC-1 is set to Flow-based, so only flow-based security scanning is available.
Step3: Configuring the root VDOM for FortiGate management
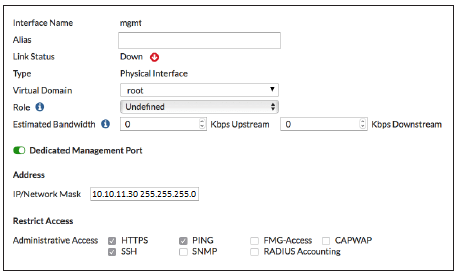
Go to Network > Interfaces. By default, all interfaces are in the root VDOM. Edit the interface you wish to use to manage the FortiGate (in the example, mgmt) and Set Administrative Access to HTTPS,PING, and SSH.
Step4: Adding interfaces to VDOM DC-1 and DC-2





LEAVE A COMMENT
Please login here to comment.