EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USViptela Security Components
In order to see the Security in SD-WAN, first we should sow what are the issue with traditional method of securing networks.
- Very little security options on authenticating of devices who are involved in communication
- Manual intervention for generating keys and passwords for securing link between devices
- Less Securely scalable and high available solutions
Viptela Security Components
There are following three Viptela security components used to secure Viptela overlay network infrastructure.
- Authentication: It allow only authentic devices to send traffic to each other.
- Encryption: All communication between devices are encrypted, secure.
- Integrity: No group keys and key servers are involved in providing security including infrastructure
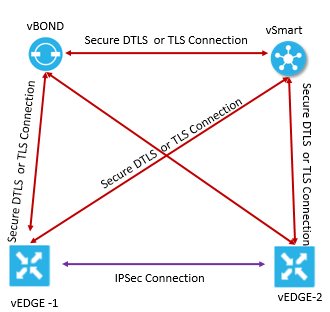
In Viptela network, the connection between devices like vBond, vSmart, vEdge in control plane and data plane are provided by Secure DTLS or TLS and IPsec method.
Security Provided by NAT Devices
In order to enhance security at branch side, a branch vEdge router can also be installed behind any NAT device. Now in this case, vEdge router can interact with NAT devices configured with method like Session Traversal Utilities for NAT (STUN) given below:
Full-Cone-NAT or One to One NAT: In this internal IP address and port is mapped to external IP address and Port.
Address-Restricted cone NAT or restricted-cone-NAT: In this internal IP address and port is mapped to external IP address and Port, but external host can send packets to the internal device only if external address has received a packet from internal address and port.
Port-restricted cone NAT: This method is highly restricted than the above NAT method, in which external host can send packet to internal address and port only if external address and port pair has received a packet from that internal address and port. In this external device must send packet from specific port to internal specific port.
Symmetric NAT:
In this each single request from same internal IP and Port to external IP and port is mapped to a unique external source IP address and port uniquely. Now when external host that receive packets from internal host can send a packet back.
In Cisco Viptela network, only one end of the NAT devices at either side of tunnel can use symmetric NAT. VEdge router behind Symmetric NAT cannot establish BFD tunnel with remote vEdge router that is behind Symmetric NAT, Port-restricted cone NAT, Address-Restricted cone NAT.
Security for Connections to External Devices
Viptela vEdge router uses Internet Key Exchange (IKE) when IPSEC tunnel between a devices with in overlay network and a device which is external to overlay network. Viptela Device uses IKEv2 to provide CIA feature that is Confidentially , data Integrity , and Authentication .




LEAVE A COMMENT
Please login here to comment.