EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSD-WAN Centralized & Localized Data Policy
Centralized Data Policy Overview:
Data Policy affects the data traffic and works on data plane of any Viptela Overlay network. There are two types of data policy:
- Centralized Data policy
- Localized Data policy
These Centralized data policy works on data plane based on IP header field in data packet on network whereas localized data policy controls traffic flow from in and out of router interface and its queues on vEdge router.
Centralized data policy is applied to packet that originates from specific sender, source Address and it controls which destination with in VPN the traffic can reach. Data policy is applied to data traffic based on 6 tuple in P packet header (IP header, Source IP, Source Port, Destination IP, Destination Port, DSCP, and Protocol)
Centralized Data policy is provisioned on vEdge router and is never pushed on vEdge router. Only the effects or decision of data policy is pushed on vEdge router. Data Policy results that is received from vSmart is applied only in inbound direction.
A centralized data policy is applied to packets that originate from a specific sender or source address. For instance, the packets could originate from a workstation at a local site that is sending voice, data, or other traffic. That workstations could also control which destinations within a VPN the traffic can reach. Data policies are applied to data traffic based on a 6-tuple of fields in the packet's IP header: source IP address, source port, destination IP address, destination port, differentiated services code point (DSCP), and protocol.
These types of policies are often used to modify traffic flow in the network. The following are some examples of the types of control that can be applied with a centralized data policy:
-
You can define the set of sources that are allowed to send traffic to any destination outside the local site. For example, local sources that are rejected by such a data policy can communicate only with hosts on the local network.
-
You can configure the set of sources that are allowed to send certain application traffic to a specific set of destinations outside the local site. For example, local sources that match this type of data policy can send voice traffic over one path and data traffic over another.
-
You can define the source addresses and source ports that are allowed to send traffic to any destination outside the local site or to a specific port at a specific destination.
In addition to examining the network and transport layer headers in data packets, a centralized data policy can be used to examine the application information in the data packets' payload. This deep packet inspection offers control over how data packets from specific applications or application families are forwarded across the network. You can then assign the traffic to be carried by specific tunnels. You can also use application-aware routing to control the traffic flow of specific application traffic that is based on the traffic loss or latency properties on a tunnel.
You can use data policies to enable many services, such as the following:
-
Service chaining
-
Network Address Translation (NAT)
-
Traffic policing and counting
-
Transport selection and traffic engineering
-
Quality of service (QoS) classification
The following figure shows the configuration components for a centralized data policy.
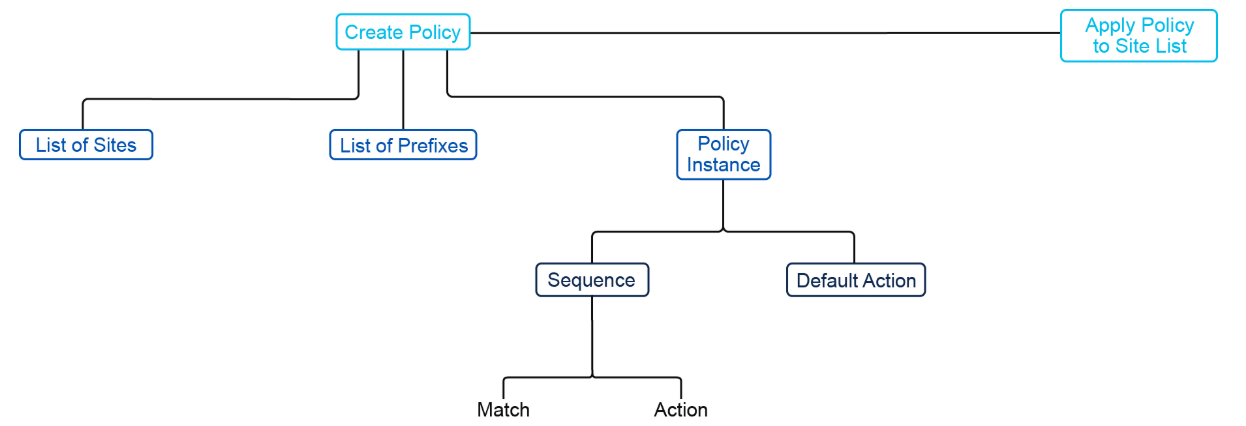
To configure centralized data policies, use the Cisco vManage policy configuration wizard. The wizard consists of sequential screens that guide you through the following process of creating and editing policy components:
-
Create Groups of Interest: Create lists that group related items and that you call in the match or action components of a policy.
-
Configure Traffic Rules: Create the match and action conditions of a policy.
-
Apply Policies to Sites and VPNs: Associate a policy with sites and VPNs in the overlay network.
In the first three policy configuration wizard screens, you are creating policy components or blocks. In the last screen, you are applying policy blocks to sites and VPNs in the overlay network. For a centralized data policy to take effect, you must then activate the policy.





LEAVE A COMMENT
Please login here to comment.