EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USTLS/SSL Inspection
Now we will focus on the TLS Description (Proxy) segment of the Zero Trust Exchange diagram.
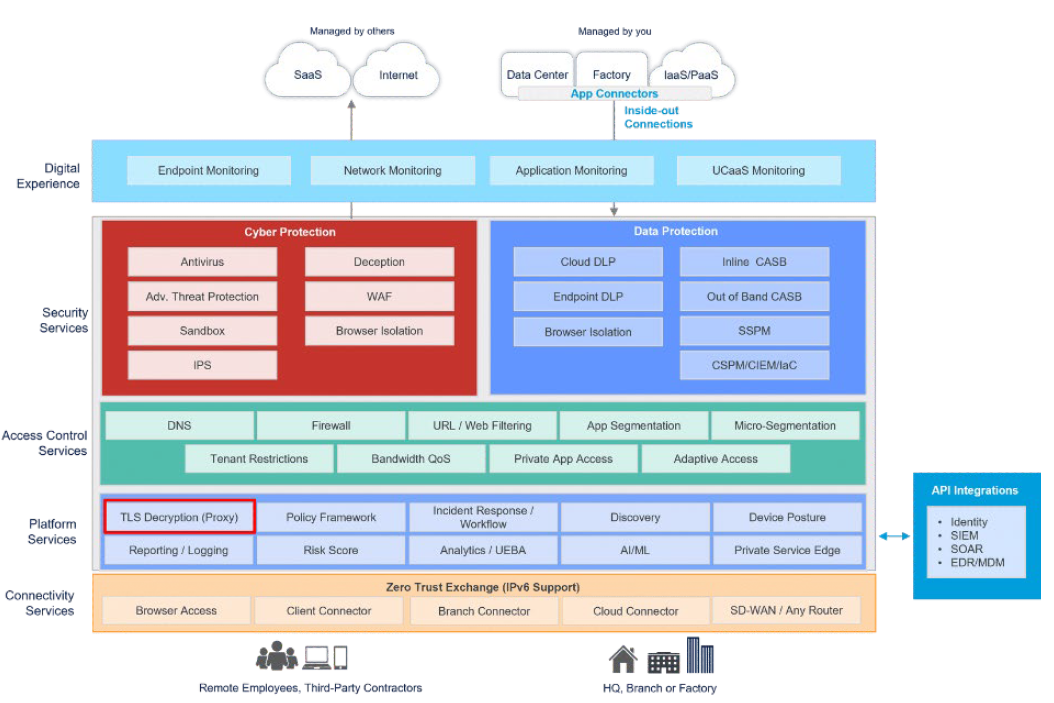
TLS Inspection, also known as SSL Inspection, is a cybersecurity practice that inspects encrypted network traffic. It involves decrypting and analyzing the contents of TLS-encrypted communications between clients and servers to detect and prevent malicious activity, such as malware or data exfiltration, that may be hidden within encrypted connections.
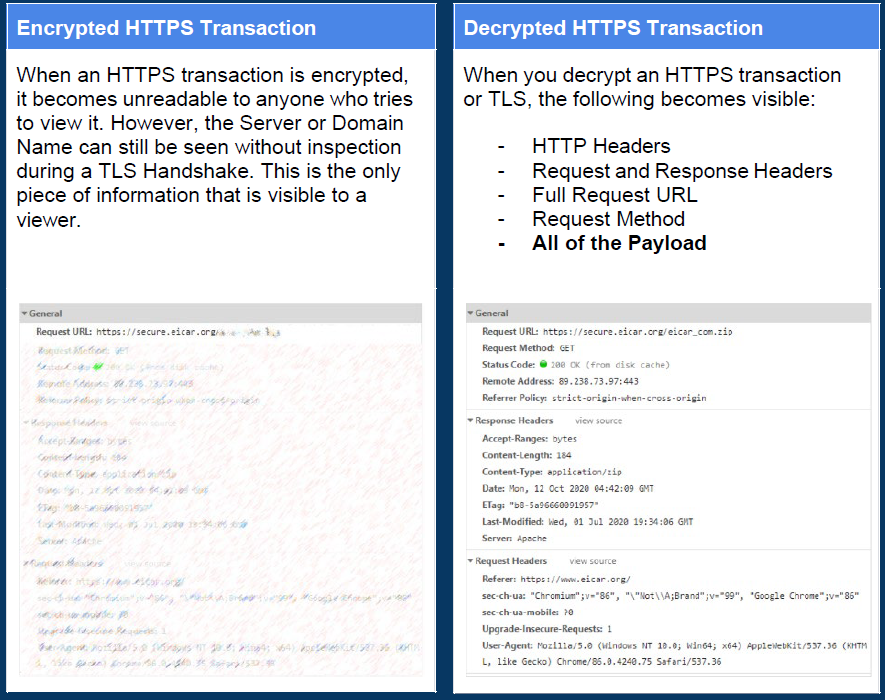
Why SSL Inspection
-
Network Visibility and Risk Control
Understanding what users access enables organizations to enforce acceptable use policies, optimize performance, and manage risk effectively. Traffic inspection combined with adaptive controls helps identify and mitigate threats in real time. -
Compliance with Security Policies
Many organizations mandate monitoring and control of all inbound and outbound traffic. Without inspecting encrypted traffic, policy enforcement becomes ineffective, increasing the risk of compliance gaps and security violations. -
Data Loss Prevention (DLP)
SSL/TLS inspection helps detect unauthorized data exfiltration and sensitive data leakage, ensuring that confidential information—such as credit card details or proprietary documents—is not transmitted inappropriately. -
Enhanced Endpoint Security
Even if endpoints are compromised, traffic inspection can block communication between infected devices and malicious servers, significantly reducing the impact of attacks. -
Tenant Restriction and SaaS Control
Organizations can restrict access to specific organizational tenants or instances of cloud services such as Microsoft 365, Google Workspace, and other SaaS applications to prevent unauthorized usage. -
Protection Against Sophisticated and Encrypted Threats
Advanced threats like ransomware frequently use encrypted channels to download payloads or communicate with command-and-control (C2) servers. Since most internet traffic now uses HTTPS, attackers exploit encryption to hide malware, phishing, and malicious communications. SSL/TLS inspection decrypts this traffic, allowing security tools to detect and block hidden threats.
SSL vs. TLS
SSL and TLS are cryptographic protocols used to secure data transmission between two endpoints. While closely related, there are important differences:
- SSL (Secure Sockets Layer) was developed by Netscape in the mid-1990s, with SSL 3.0 released in 1996.
- TLS (Transport Layer Security) was introduced in 1999 as an improved successor to SSL.
- TLS 1.3, released by the IETF in 2018, is the most secure and current version.
All versions of SSL were officially deprecated by the IETF by 2015 due to known vulnerabilities, including susceptibility to man-in-the-middle attacks. Although SSL is no longer supported, the term “SSL” is still commonly used as a generic reference to encrypted communications. For accuracy, this document uses TLS to describe the protocol, while the term “SSL Inspection” is retained to describe the inspection of TLS-encrypted traffic.
Zscaler and TLS Decryption
As part of Zscaler’s Platform Services, TLS Decryption (Inspection) enables Access Control, Cyber Protection, and Data Protection policies to be applied based on the actual content of encrypted traffic.
Why TLS Inspection Matters
Consider a real-world example:
When a user downloads a PDF file from Google Drive using Google Chrome, Zscaler decrypts the traffic and inspects the file contents. This allows Zscaler to:
- Determine whether the file is malicious
- Detonate and analyze suspicious files
- Identify sensitive data within the file
- Enforce data protection policies as needed
The need for TLS inspection has increased significantly due to the rapid growth of encrypted traffic. Today, 85–90% of internet traffic is encrypted, driven by:
- Browser warnings for non-HTTPS websites
- Free certificate services such as Let’s Encrypt
- Protocols like HTTP/2, which operate exclusively over TLS
While encryption improves privacy, it also introduces visibility gaps. Attackers exploit encrypted channels to deliver malware and conduct covert operations, leading to a sharp rise in encrypted threats. Zscaler ThreatLabz’ annual State of Encrypted Attacks report consistently highlights year-over-year growth in threats hidden within encrypted traffic.
TLS Inspection Pillars and Functionalities
Zscaler recognizes that achieving strong security posture and full visibility into applications and threats requires comprehensive TLS inspection. To address this, Zscaler provides dedicated TLS Inspection pillars and functionalities designed to deliver deep visibility, advanced threat protection, and effective data security.
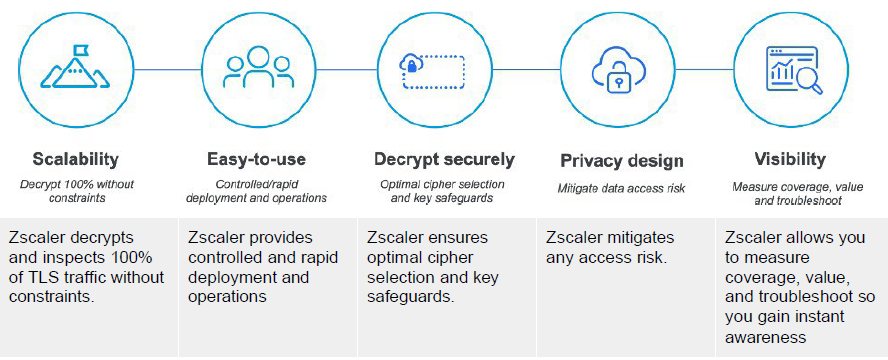
The TLS inspection capabilities within the Zero Trust Exchange span access control, threat prevention, data loss protection, and the SSL/TLS inspection mechanisms used by Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA). These capabilities include SSL interception and certificate validation in both forward proxy and reverse proxy deployment models.
Access decisions are based on trust and risk assessment. Trusted sites are granted direct access as they present lower security risk, while other sites are subject to conditional access, restricted access, or outright blocking based on their risk profile and policy evaluation.
Within the Zero Trust Exchange, TLS inspection operates across multiple functional layers. The first is Access Control, which includes URL filtering and cloud firewall capabilities. These controls allow policies to be enforced dynamically based on both the request and the response, enabling granular and context-aware security enforcement.
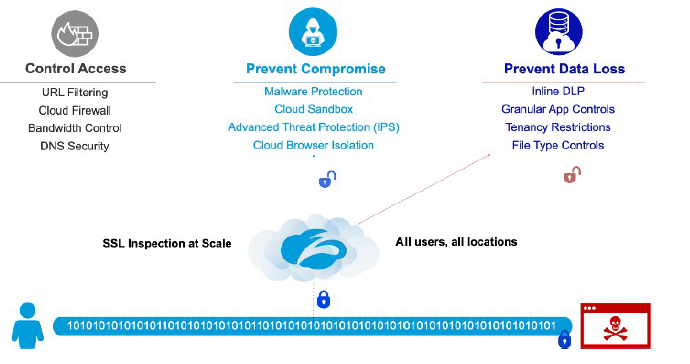
The second functional area focuses on compromise prevention. This includes inspecting the actual payload flowing to and from web servers for threats such as malware and viruses, leveraging Advanced Threat Protection (ATP), IPS signatures, and cloud sandboxing capabilities. Downloaded content can be analyzed in a sandbox environment to identify malicious behavior before it reaches the user.
TLS inspection also enables visibility into peer-to-peer communications commonly used by compromised endpoints to communicate with command-and-control (C2) infrastructure. Based on risk assessment, users can be dynamically redirected into an isolated browser container, protecting both the user and the destination application from potential attacks.
Data Loss Prevention and Data Protection
The next area is Data Loss Prevention (DLP) and data protection. Inline DLP scans outbound payloads from clients to detect and prevent both malicious and accidental data leakage to the internet.





LEAVE A COMMENT
Please login here to comment.