EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSecure Private App Access (ZPA)
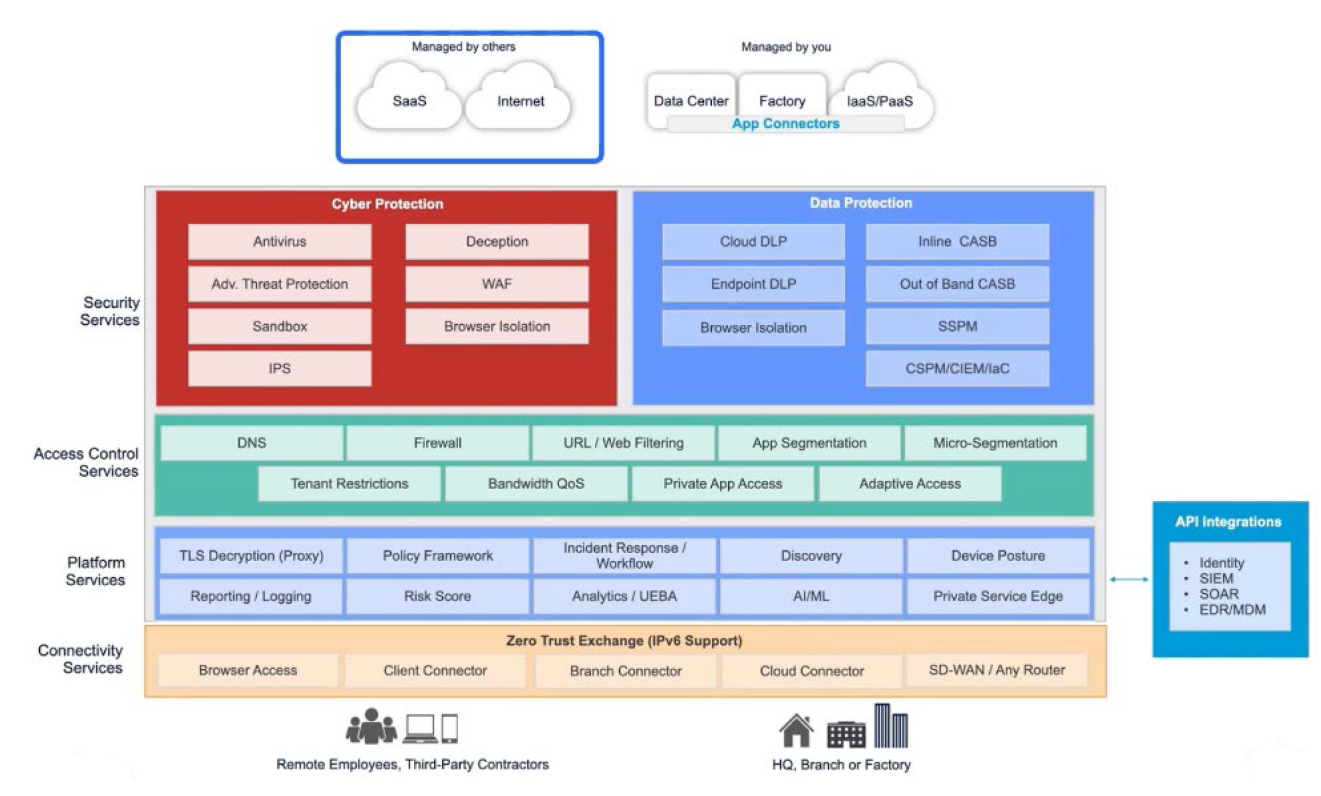
Zscaler Private Access (ZPA) delivers seamless, secure connectivity to private applications, services, and OT systems using the industry’s leading next‑generation Zero Trust Network Access (ZTNA) platform.
When we look at secure access as part of the broader Zscaler for Users ecosystem, ZPA works alongside Zscaler Internet Access (ZIA) and Zscaler Digital Experience (ZDX). After building our internet access platform, we recognized that the same Zero Trust principles and technologies could be extended to private application access—and that’s exactly what we did.
The Zero Trust Exchange, which underpins the entire platform, applies its full set of capabilities to private access scenarios as well. This includes granular access control, advanced security services, data protection, and end‑to‑end digital experience monitoring—all tailored to the private application environment.
How private access works
When a corporate user attempts to reach a private application, Zscaler Private Access (ZPA) first terminates the connection and evaluates identity, context, and security posture. Only after this verification does ZPA establish a secure, inside‑out connection through an App Connector—meaning the application is never exposed to the internet and no public IP is required.
This architecture unlocks a wide range of benefits. It delivers true Zero Trust application access and replaces legacy VPN‑based models by enabling direct, secure connectivity to private and cloud‑hosted apps—without the need for DMZs, inbound firewalls, or other traditional perimeter appliances. Many organizations have replaced both their VPN and portions of their VDI infrastructure with ZPA, because the App Connector can broker RDP, SSH, and even full web sessions, providing Zero Trust access to applications running on ports such as 80 and 443.
ZPA can also be deployed locally through a Private Service Edge, allowing traffic to stay entirely on‑premises while still benefiting from Zero Trust policy enforcement, without hairpinning to the cloud. This flexibility extends to third‑party users, suppliers, and unmanaged devices—ZPA can grant tightly scoped access to only the authorized applications while keeping them off the network entirely.
This shift eliminates the need for VPNs, private interconnects, and complex network merges during activities such as M&A. Organizations adopt ZPA because it reduces security risk, increases productivity, lowers operational costs, and consolidates multiple point products—all through a unified Zscaler for Users deployment.




LEAVE A COMMENT
Please login here to comment.