EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USZTDA Identity Services
Identity integration in Zscaler enables secure authentication and authorization of users to the Zero Trust Exchange (ZTE). It ensures that only the right users, with the right attributes, can access the right applications based on dynamic policy.
This Identity Services module covers three core areas:
- Introduction to Identity Integration
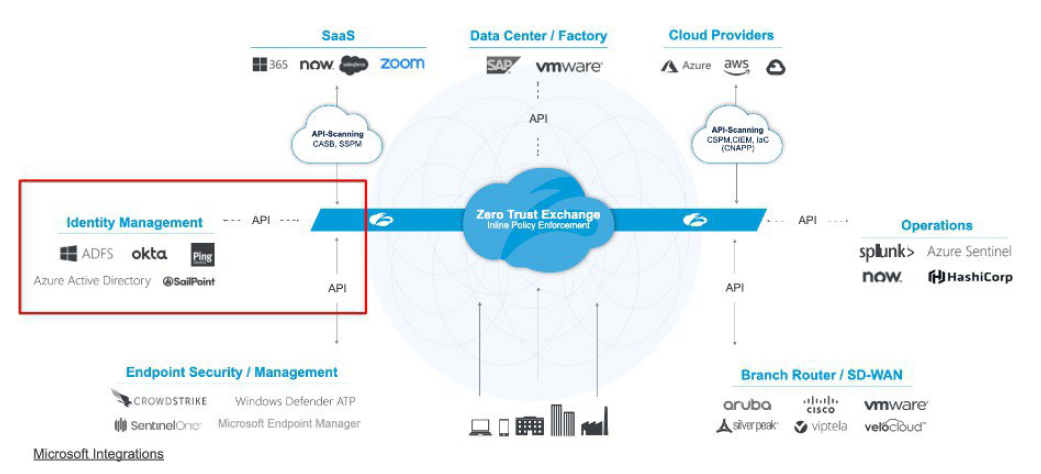
Zscaler connects with Identity Providers (IdPs) to verify users and apply context‑based access policies. User and device attributes—such as group membership, posture, and location—are consumed to enforce fine‑grained security controls. - SAML Authentication
Zscaler uses SAML (Security Assertion Markup Language) to authenticate users securely. This supports seamless single sign‑on (SSO) across applications, allowing users to access multiple services without repeated logins. - SCIM Authorization
SCIM (System for Cross‑domain Identity Management) keeps user identities synchronized across platforms. It automates user provisioning, deprovisioning, and attribute updates—ensuring policies remain aligned with each user’s current role and access needs.
Overall, identity integration ensures secure, consistent, and efficient user access within Zscaler’s Zero Trust architecture, supporting strong authentication, accurate policy enforcement, and streamlined identity lifecycle management.
Connecting to an Identity Provider
Before configuring Identity Provider integrations, it's important to understand how Zscaler for Users enables secure connectivity to the internet, SaaS applications, and private applications. Users can reach applications either directly through options like Direct Connect or ExpressRoute at cloud or data‑center environments, or through the Zscaler Client Connector or a browser connecting to the Zero Trust Exchange (ZTE).
When a user connects to the ZTE, the first step is identity and context verification. This is typically done using a SAML Identity Provider, though Zscaler Internet Access (ZIA) can also authenticate using LDAP or a hosted user database. Once the user’s identity and attributes are validated, Zscaler applies risk controls—including traffic inspection and data protection—and enforces policies such as Allow, Block, Isolate, and Prioritize based on user and device context.
From there:
- ZIA governs access to internet and SaaS applications, leveraging user and device attributes for dynamic policy.
- Zscaler Private Access (ZPA) provides secure, policy‑based connectivity to private applications hosted in IaaS, PaaS, or private data centers.
Overall, identity verification forms the foundation of Zero Trust, ensuring that all access decisions are made based on validated identity and real‑time context.
Zscaler Digital Experience (ZDX) provides deep visibility into the end‑user experience, including device performance, network connectivity quality, and factors causing latency when accessing internet, SaaS, or private applications. It helps IT teams understand how users interact with applications and quickly identify bottlenecks or performance issues.





LEAVE A COMMENT
Please login here to comment.