EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USSecurity Groups & Firewall Services
Task:
- Configure Neutron to enable Firewall services.
- Create a security Group dclessons-SG1 and add following rules to allow 80 services with source and destination any any via GUI
- Create a security Group dclessons-SG2 and add following rules to allow 443 services with source and destination any any via CLI
- Apply the security group dclessons-SG1 on dclessons-VM1
- Create Firewall Rule dclessons-FW-RULE1 to allow TCP protocols for source any and destination 40.40.40.0/24 network port 22.
- Create Firewall policy dclessons-FW-Policy1 and call the above FW rule created.
- Now Create the FW and apply the above policy created and verify rule on network nodes.
Solution:
To configure the Firewall services on Neutron, modify the following file as per given below:
[DEFAULT]
...
service_plugins = firewall
!
[service_providers]
...
service_provider = FIREWALL:Iptables:neutron.agent.linux.iptables_firewall.OVSHybridIptablesFirewallDriver:default
!
[fwaas]
driver = neutron_fwaas.services.firewall.drivers.linux.iptables_fwaas.IptablesFwaasDriver
enabled = True
!
[root@localhost ~(keystone_admin)]# sudo nano /etc/neutron/l3_agent.ini
[DEFAULT]
...
interface_driver = neutron.agent.linux.interface.OVSInterfaceDriver
To configure the Horizon dashboard for Firewall, open the /usr/share/openstack dashboard/openstack_dashboard/local/local_settings.py file and set an enable_firewall option in the OPENSTACK_NEUTRON_NETWORK setting:
'enable_firewall' = True
restart neutron-server, neutron-l3-agent, and horizon for the changes to take effect.
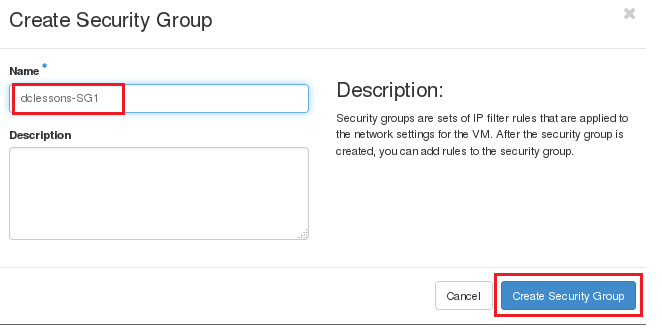
Now to configure the Security group go to Project | Compute | Access & Security and In the Security Groups tab, click on + Create Security Group.
Fill in an appropriate security group Name and Description:
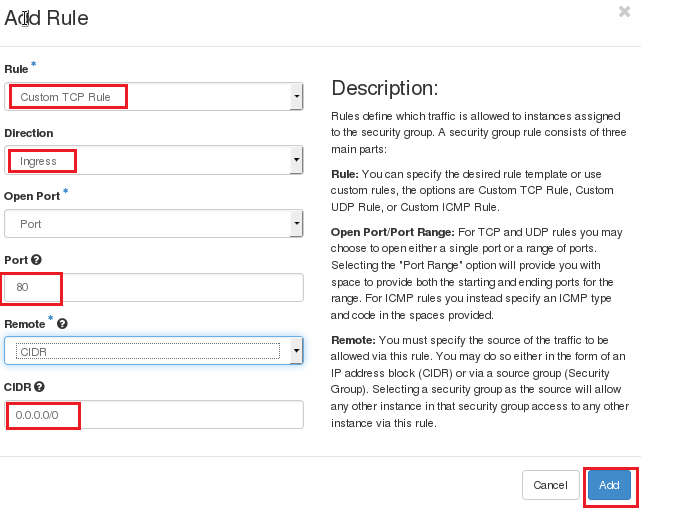
Now to add rules on SG click on SG you created and then click on manage rule and then ADD rules.
Now create another SG via CLI to open port 443.





LEAVE A COMMENT
Please login here to comment.