EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USOpenStack Clustering:
In the OpenStack clustering, one or more servers is combined or aggregated together to form High Availability Cluster. There are two types of clustering mechanics used:
Asymmetric Clustering:
This type of clustering is used in HA purpose and also for read/Write operations in databases, different files and other systems.
In this Standby server will be active only when Primary server went sown or will face service failure.
Symmetric Clustering:
In this all servers or nodes are acting as active servers, and handles all requests. Once any node is failed, it gets removed from cluster and others will take over its requests. This type of clustering also acts as load balancing cluster.
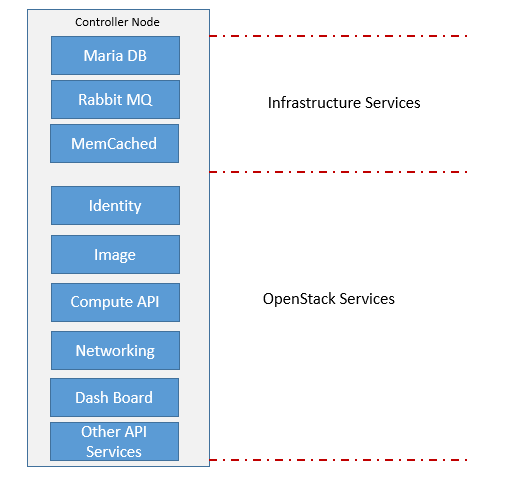
Cloud Controller:
Cloud Controllers acts as a central management server and also helps in OpenStack deployment. It manages all API calls and other messaging transactions.
Following are the Cloud Controller functions:
- It provides all type of API services which helps in communication between all OpenStack components.
- It provides Services interface to End user or tenants.
- It also helps in providing HA and load balancing services
- It provides infrastructure services like database and message queue.
- It exposes persistence storage.
Keystone Services:
Keystone is the service which provides the identity services and service cataloging. Keystone provides rule based access and authorization of services to OpenStack. In open stack all services register with Keystone along with their API endpoints so that they can communicate with each other.
Keystone itself is composed of multiple providers like:
- Identity
- Resource
- Authorization
- Token
- Policy
- Catalog
Identity Provider:
The main function of Identity provider is to create and authenticate users and group credentials. It can also be integrated by external identity providers like LDAP. Following are the various user’s type keystone supports.
- Service User who is using Services running in OpenStack
- End User who is acting as external user.
- Admin user who need to access the services and resources for integrating customers and support.





LEAVE A COMMENT
Please login here to comment.