EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USVXLAN BGP-EVPN Multitenancy
Bridge Domains:
Bridge Domain is said to be a broadcast domain that represents the scope of L2 network. In VXLAN network the Bridge domain extends up to 16 Million, segments of VNI. So with respect to VLAN, there are two types of encapsulation exits to allow mapping from VLAN to VNI and vice versa. This mapping is always configured on edge device or VTEP.
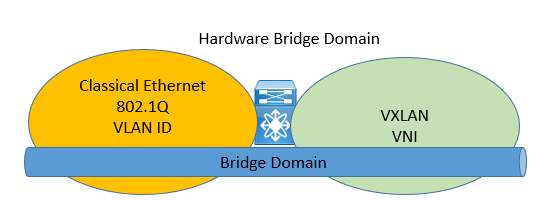
In VXLAN, the bridge domain consists of three components:
- The classical ethernet domain with the VLAN namespace
- VXLAN domain with the VNI name space
- Network switch with hardware/software bridge domain resource.
VLAN in VXLAN:
Most Servers send ethernet traffic which is encapsulated in certain VLAN. In ethernet segment VLAN must be spread across networks switch inorder to send the VLAN traffic from one switch to another with a limitation of 4K VLAN boundary.
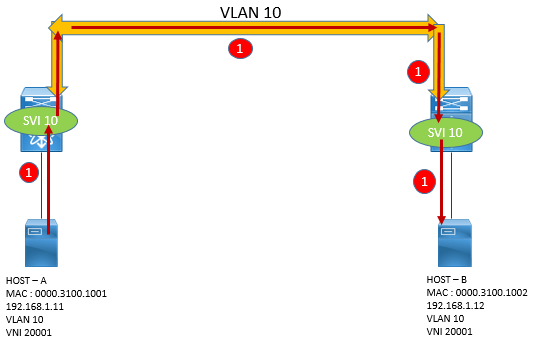
With VXLAN, the VLAN became the Local identifier and VXLAN VNI becomes the Global identifier. All ends points that needs to communicate to each other must be in same Layer 2 VNI.
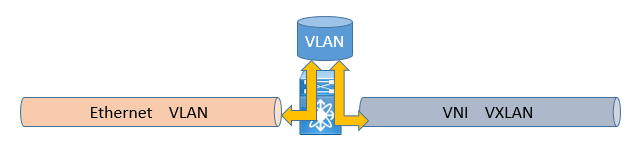
On a given edge device, 1:1 mapping between VLAN and VXLAN must be done.
vlan 10
vn-segment 10001
vlan 20
vn-segment 20002
In this way, the VLAN is the local identifier, and the VNI becomes the global identifier. The VLAN is now significant to that edge device only. In this way, different VLANs on different edge devices can map to the same VNI
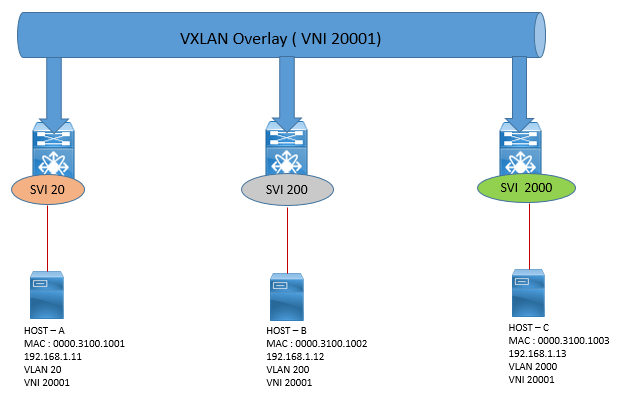
Per-port VLAN uses the VLAN ID arriving on the wire that is stored in the dot1q header. The edge device immediately maps this wire VLAN to an encapsulation independent identifier without creating this VLAN on the switch and maps the wire VLAN to a VNI.
In the below figure the same VLAN 10 on two different ports (Ethernet 1/1 and Ethernet 1/2) maps to VNIs 20001 and 20002 respectively.
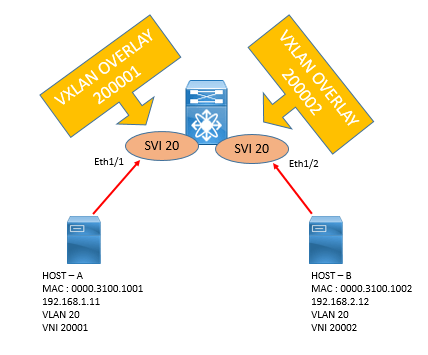
Sample Layer 2 VNI Configuration with per-Port VLAN Significance
vlan 3201
vn-segment 20001
vlan 3202
vn-segment 20002
!
interface Ethernet 1/8
switchport mode trunk
switchport vlan mapping enable
switchport vlan mapping 20 3201
!
interface Ethernet 1/9
switchport mode trunk
switchport vlan mapping enable
switchport vlan mapping 20 3202
To advertise the L2VNI in the BGP-based EVPN address family, configuration of the MAC-based EVPN instance is done. In order to uniquely identify the EVPN instance (EVI) within MP-BGP, the instance consists of a VNI (L2VNI) and a Route Distinguisher. In order to support MP-BGP route policies, appropriate Route Targets are defined to ensure that prefixes for the instances are being imported. The values chosen for the EVI are unique for the given instance because they are unique to the L2VNI.
Sample Configuration to Advertise Layer 2 VNI Routes into BGP EVPN
evpn
vni 10001 L2
rd auto
route-target import auto
route-target export auto
vni 20002 L2
rd auto
route-target import auto
route-target export auto
With the Cisco implementation of BGP-EVPN, the Route Distinguisher (RD) and route target (RT) values are derived automatically. The RD is generated from the router ID and the internal Layer 2 instance ID. The RT is derived from the autonomous system number (ASN) of BGP and the Layer 2 VNI (L2VNI). Note
that if eBGP is employed for the underlay, the RTs need to be manually configured because the ASN may be different for different edge devices.





LEAVE A COMMENT
Please login here to comment.