EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USPolicies-Filters & Endpoint Security
How Fortigate Process data packet:
Fortigate process the data packet based on following steps:
- Ingress: When packet comes on Fortigate, ingress filtering controls the network from various security ricks like DOS attack, IPsec Security, unwanted packet traversing to our internal network. After the Security and access check routing is performed on the Ingress Level.
- Stateful Inspection engine: Fortigate is stateful inspection engine, any traffic going from inside to outside, its connection state is maintained, and on returning packet no ACL or filtering is done.
- UTM Scanning : Fortigate has preconfigured UTM Profiles which in turn helps us in various features like antivirus , Web filtering , Email Filtering , IPS etc.
- Egress: One a data packet is moving to outside to fortigate , it performs egress filtering along with security checks on NAT Sources , IPSEC and then performs the routing to send data finally out of the box.
Zones in Fortigate:
Zones are groups of multiple interface (physical, logical, VLAN, VPN Tunnel) which requires same security policies from incoming and outgoing traffic.
To create Zone follow these steps:
System | Network | Interface and then click Zone.
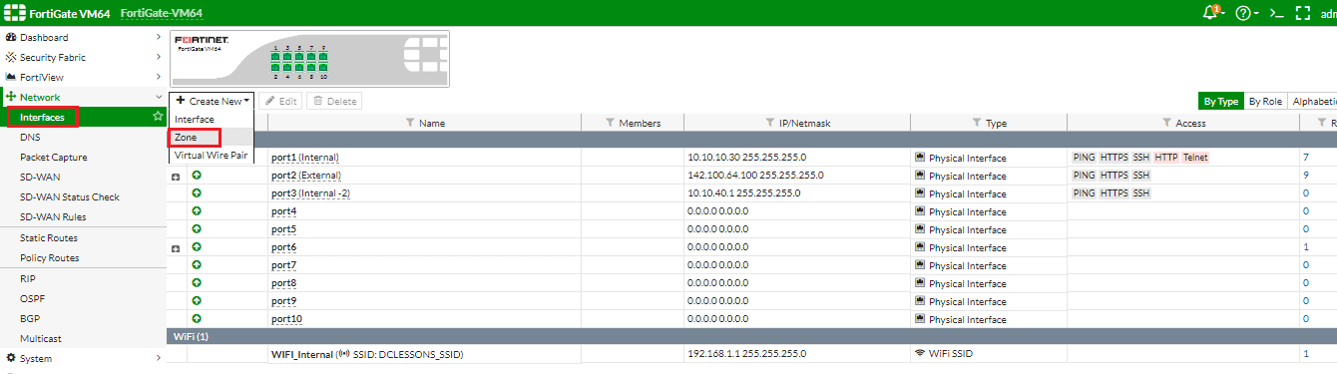
In the zone configuration we can selects the Block intra-zones traffic option to prohibit the different interfaces in the same zone to communicate to each other.
Addresses:
Addresses are used in fortigate to group IP range, or FQDN or it contain single address also. FQDN helps to create rules, policies for internet servers and to manage policies in larger network environment.

Comment
You are will be the first.




LEAVE A COMMENT
Please login here to comment.