EMAIL SUPPORT
dclessons@dclessons.comLOCATION
USF5 High-Availability
In Most BIG IP F5 deployments, they are deployed in in pairs to provide redundancy, resiliency, against individual failures. Now once the failure is detected, a F5 device failover can be initiated automatically (manual Failure is also possible).
The Pairing can be done in some more ways like, an Active-Stand by Setup, or Active-Active Setup. We will learn these setup in more details in coming sections.
Below figure defines Active-Standby Network Design.
Configuring a Sync-Failover Pair
When we plan to configure HA-pair for F5, there are certain things that have to be configured to get system up and running.
Device Trust
A trust has be established between two F5 members in order to configure them in to any device group (sync-Failover or Sync-Only). This Device trust is established with Certificate based authentication through the signing and exchanging of x509 Certificates.
Device who trust each other are part of a trust domain, and these devices can synchronize configuration, exchanges failover message, and failover to each other when necessary.
Trust Authorities
While creating a device trust, we have two options to select the Trust Authorities as given below:
Certificate Signing Authorities
When F5 is configured as CA, it will be able to sign x509, Certificates for another BIG IP systems, due to which it will be able to add F5 to local trust domain.
Peer Authorities
Whenever two CSA established a trust with each other, they are said to be peers to each other. If one F5 system fails, other will acts as backup and can still add new F5 devices to device trust.
Subordinate Non-Authority
Adding new F5 devices in to device trust, can be a security risk, when a F5 devices are placed in to lower security Zones. In this case you can join F5 device as Subordinate Non-Authority, hence this device will not be able to add new devices.
Device Identity
In each F5 devices, x509 Certificate are installed in order to identify themselves, with in domain trust. Device identity are combination of both x509 certificates and additional information such as:
- Device Name
- Host Name
- Platform Serial Number
- Platform MAC address
- Certificate Name
- Subjects
- Expiration
- Certificate Serial Number
- Signature Status
Device Discovery Process in Local Trust Domain
F5 joins a local trust domain by using a process called Device Discovery. During this process F5 system and peers exchange their device properties are device Connectivity information.
When all peers shares the information to each other, and if F5 system joins a local trust domain that already two F5 system , the system joining device trust will exchange device properties with other two F5 system , which are already part of Local trust domain.
After the exchange, F5 system that joined the local trust domain, will have three set of device properties now.
When we configure the device trust, following things needs to be consider.
- F5 system running v11.x and above can join local trust domain.
- When a device is configured as Subordinate non-authority device, we cannot manage device trust via this device. This can only be done through a certificate signing authority.
- Before you a new device to local trust domain, don’t forget to configure config sync, Failover and Mirroring address.
Resetting the Device Trust
When you need to reset the device in order to manage the certificate authority of F5 that are part of local trust domain. Some task include:
- Regenerate the self-signed certificate on a device
- Import a user-defined certificate authority
- Retain the current authority
Device Groups
Once device groups are configured, now it is required to assign them to a device group. There are two types of device groups:
Sync-Only Device Group:
Device assigned to this group synchronize configuration data and have up to 32 devices. Devices in the trust domain can be a member of more than one sync-only device group and devices that are part of device failover group can simultaneously be member of Sync-Only Device group.
Sync-Failover Device Group:
When we configure HA pair, we must use Sync-Failover device group. This device group will synchronize configuration data and failover objects. When Primary device is unavailable, Secondary node will handle all traffic. A Sync-Failover device group can contain up to 8 objects.
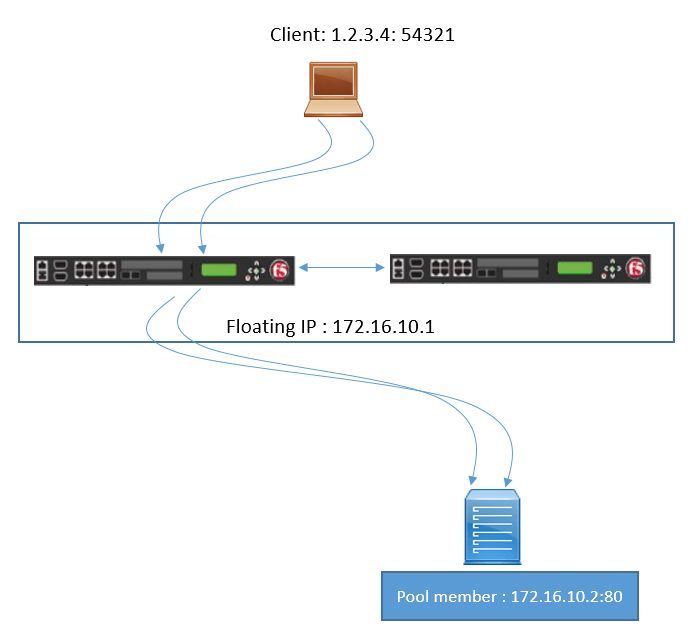
Floating IP address
Floating Self-IP address are configured on the device where the traffic group is assigned. This address will always available on the active system in HA pair.
When a failover occurs, MAC address of the floating IP address will change and here with the Gratuitous ARP, all other systems are informed about change in MAC address and their ARP table is updated.





LEAVE A COMMENT
Please login here to comment.